Online scams and identity theft attempts have risen multifold in recent times. Here, cyber-criminals are trying all new ways to attack users to steal their identity traces. To do this, they may attack users with ransomware, spyware, phishing attempts, or other malware. When you know the threat is real, it becomes important to take preventive measures. In this article, we have reviewed some of these effective steps that will help you keep yourself protected against scams and identity theft. Following these steps, you can easily keep your valuable information safe from cyber-criminals & cyber threats.
Avoid Suspicious Links
Cyber-criminals send you malicious links & attachments where they ask you to open attachments or click on links. Once you click on these links or open these attachments, your system gets affected with malware. Thus, it is better choice to avoid clicking links or attachments sent through unknown or suspicious senders. It will help you avoid unnecessary troubles effortlessly.

Avoid Open Network
Open network like free Wi-Fi sounds lucrative deal but it brings lot of security issues for you. Here, it becomes really easy for criminals to affect your device and breach your system security with a small piece of malicious software. Thus, we suggest you should avoid open networks especially when you are doing sensitive transactions like banking, shopping and similar activities.

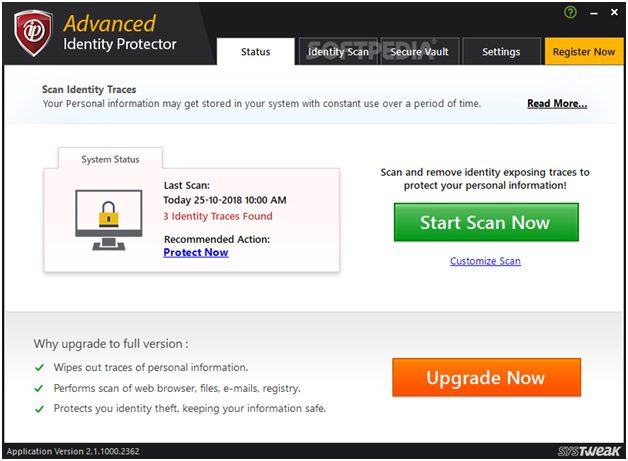
Install Identity Theft Protection Software
Next best solution to avoid scams and identity theft is to use best identity theft protection services. These smart tools work on advanced algorithms to help you find & secure all identity traces on your device. Here, it deeply scans your device storage to find all identity traces and help you keep them secure in a secured vault. These vaults remain secure with encryption to keep your important data away from cyber-criminals
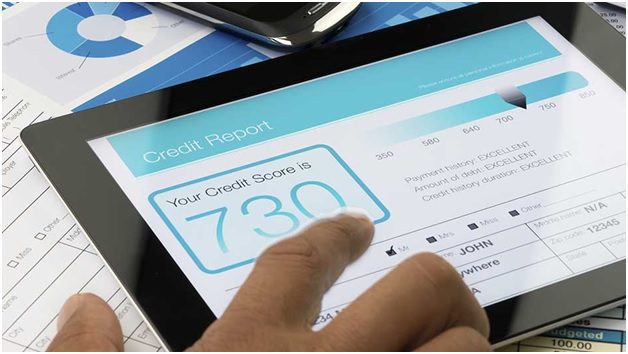
Monitor Credit Score
Your credit score gives your insight about your credit worthiness based on your financial condition. Here, it keeps on changing when you avail financial services. Thus, it becomes important to monitor your credit score at regular intervals to know if something suspicious is going on. It is possible that criminals may avail finance services using your identity proofs in fraud manner, thus we suggest you should apply for regular credit reports and check credit score to check if everything is okay.
Use Strong Passwords
Using strong passwords not only helps you keep your data safe from online threats, but it also helps you avoid unnecessary trouble from curious onlookers. Here, we suggest you should use at least 8 characters password that includes letters, numbers, special characters for better security. You should also use different passwords for different accounts. You can even use password manager tools to manage your passwords in one place.

Shred Files Properly
This is important tip no matter you are shredding documents online or offline. Here, you should ensure that whatever document you find unnecessary should be shredded properly. For online file shredding, you can use reliable file shredding services. These advanced tools work on military-grade shred features to help you remove data permanently.

Update Software
Outdated software not only brings performance issues, but it also causes security problems on your system. Here, it becomes really easy for cyber-criminals to breach system security with known loopholes on older software. Thus, you should be proactive to install all software updates you receive at regular intervals. You can also update software manually when needed.
Download from Trusted Sources
Never ever download or install software or program from untrusted source. Here, all major device manufacturers offer their own stores to help you buy software & apps. Thus, you should always prefer these platforms to install anything you want for your system.

Scan Device for Malicious Content
Under this option, you can scan your device using reliable anti-malware software. It will help you find all malicious content on your system and even helps you fix the problem. You can do it at regular intervals, or you can even schedule the scan process to save time.

Set Guest User Account
Don’t always rely to work on your system using administrator account instead you should create a guest account on your device for people who want to use your system. It happens many times when malware spreads on your system using administrator privileges thus when you allow people to work on a guest account, you can restrict them to limited permissions.
Conclusion
Following some simple yet effective steps, you can easily manage to protect yourself from scams and identity theft attempts. Here, we have discussed some of these steps in detail. If you know more such steps, then feel free to comment below.
About Author: –
Chandra Shekhar Choudhary is working as an SEO analyst and technical Content Writer. His potential of writing is PC tips, Android and Mac tricks , CPU benchmark and he is anxious in writing other technical blogs. You can also find Chandra Shekhar on Facebook, Twitter and Instagram.
