Summary
WordPress is constantly being attacked, left and right. WordPress security thus cannot be overlooked. There are various security features and protocols but vulnerabilities are even more numerous. Knowing what these are is the first step to keeping your WordPress website secure. The next step is to implement measures to safeguard them. Both these critical steps are covered—plus some additional steps–here.

Two-fifths of all websites and nearly two-thirds of websites that use a content management system are built using WordPress—or over 800 million websites. This popularity attracts cyber-crooks in droves, with nearly half a dozen sites being hacked every year.
Who are these targets? Everybody. Every site—including yours—is vulnerable; if a site is exploitable, it’ll be exploited. But falling prey to hackers is not an inevitability. Attacks can be thwarted and breaches prevented. Understanding what makes a website susceptible and closing possible loopholes can go a long way to forestall malicious actors.
What makes a website vulnerable
It shouldn’t take a breach to identify the vulnerabilities. Website security is too important a thing to let it be breached, even if a valuable lesson is learned because of it. You need to be defensively proactive, not merely reactive.
To proactively defend your site from attacks, you need to be aware of all the possible vulnerabilities and either reinforce or remove them—yes, all of them. Different weaknesses have different degrees of severity should a breach occur and multiple flaws increase the susceptibility to hacking, but oftentimes a defect is enough to wreck your website.
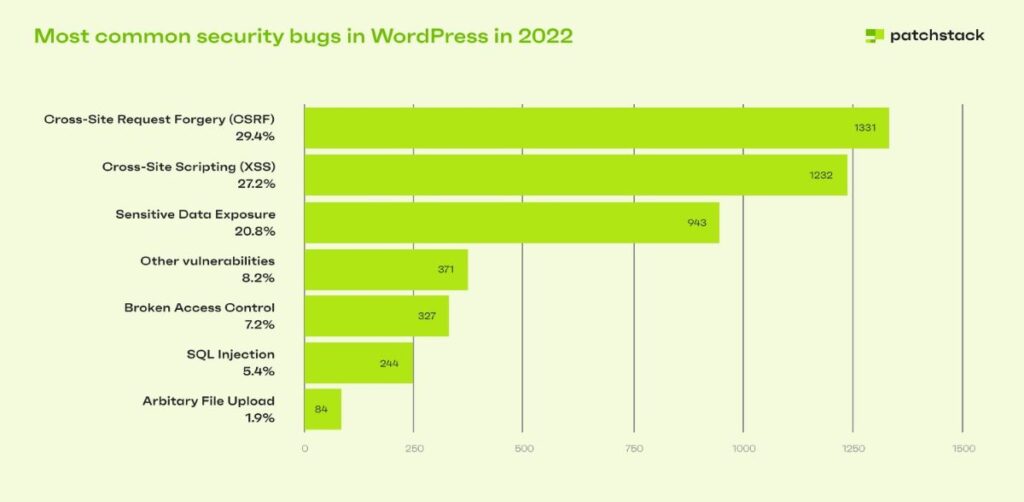
Source: Patchstack
There are several things or factors that render your website permeable. The following are some major security risks and attacks, selected for their exploitability and high potential impact. It may be noted here that special expertise may be required to safeguard your website and partnering with reliable WordPress development service providers for a thorough diagnosis and remediation might be the most viable choice.
Untrusted or outdated plugins and themes
Plugins are the most common backdoors for threats to enter. According to a 2022 WordPress Security report by Patchstack, a cybersecurity firm, 93 percent of security bugs were found in plugins, themes accounted for 6.7 percent, and only 0.6 percent is attributable to WordPress core.
Bundling malicious code, often unintentionally when developers use third-party code from libraries (say), with the plugin or theme is one way bad actors gain access to your site. But it is far from the only one. Vulnerabilities in outdated add-ons may be exploited to inject malicious code into your website.
SQL injection
This is one of the oldest forms of attack and is still prevalent. An SQL injection is a malicious code that is inserted via certain input forms—e.g. username, contact form, comment—and gives the attacker the ability to modify the database. This allows them to alter existing data, add new information, and delete or disclose all data in the database.
Cross-site request forgery
In cross-site request forgery (CSRF) attacks, the attacker tricks an unsuspecting user into executing unwanted actions. As the request is authenticated by the website, a forged request cannot be distinguished from a legitimate one.
The attacker can cause the user to change their credentials, edit or delete data, or perform actions masquerading as the user. Depending on the user and the actions they take, CSRF attacks can be devastating. For example, if the user is an admin, then the attacker can completely take over the site.
Cross-site scripting
Vulnerabilities due to cross-site scripting (XSS) are easily introduced and they are also greatly exploited by hackers—XSS attacks are one of the most common. These vulnerabilities allow attackers to intercept user interactions and inject malicious scripts. This enables them to steal cookies, hijack users’ sessions and perform actions on their behalf, and grab their credentials.
Shared hosting
Sharing a hosting with other websites can introduce a host of security issues. Not only do you have limited control over the server configurations and implementing specific security measures, but the co-habitation means that an infection of one site can spread to the others.
And because there is a contention for resources, sites may be more susceptible to DDoS attacks. The sharing of resources also means that if one website is subject to a DDoS attack, then the whole server may either suffer downtime or reduced performance.
The above ones are by no means exhaustive and did not include some common quotidian vulnerabilities such as weak passwords, leaving the default settings unchanged, outdated software, and lack of SSL certification among others. The vulnerabilities are many but luckily we need not go to great lengths to make a website secure.
How to make your site secure
WordPress has several security features and protocols to help protect websites from malicious actors. This includes measures such as the following.
- Encrypted data transmission between the server and the user’s browser
- Content security policy to allow website owners to control which sources of content can be loaded on their site
- CSRF protection using cryptographic tokens called nonces, which upon logging out are invalidated
- Limiting login attempts and multiple-factor authentication support to thwart brute force attacks
- Secure session management techniques to prevent session hijacking
These are great but they are obviously not enough to make a website impervious to attacks, as the frequency and magnitude of security breaches show. You, as the website owner, play a crucial role in keeping it safe and secure.
And there is much that you can do. Most of this doesn’t require technical expertise or heavy investment. For the utmost security guarantee, you may need to hire a WordPress developer or an expert with the requisite skills for regular housekeeping or inspection.
Keep WordPress and add-ons up-to-date
WordPress releases updates about every three months. These roll out new features and improve performance but more often than not they include bug fixes and security enhancements. Keep a tap on the releases and install the updates when they are available. Enable automatic updates so that you don’t have to worry about it.
Equally, perhaps more, important to make sure that the plugins and themes are up to date, as these are the Achilles heel. Attacks often happen through them and it is they that give way.
Install SSL certificate
Secure sockets layer or SSL ensures that the data transmitted between the visitors and the website are encrypted, intact, and unaltered during transit. This helps secure communication and prevents any unauthorized tampering or interception of the information.
Sites with SSL certificate installed use HTTPS. You can thus easily identify if your site has an SSL certificate. Ensure that all internal links and resources use HTTPS. Additionally, implement HTTP Strict Transport Security or HSTS to help ensure that web browsers connect with your website using an HTTPS connection. This helps protect your site from protocol downgrade attacks and cookie hijacking.
Configure user roles and access control
Properly configuring user roles in WordPress and defining levels of access and permissions is necessary to maintain the integrity of your website. Grant permissions to specific users only those necessary for the role—nothing more. And review and update the permissions regularly. If, for instance, you have contributing writers, it’s not a wise move to lavish them with many permissions; it can be confusing for the author and potentially destructive for the site. In most cases, only administrators need access to website configuration, themes, and plugins.
Granular access control ensures that users only have the permissions they need to do their job. This prevents accidental tampering with the website’s configuration or making changes that could compromise the security. It also limits damage in the case of unauthorized access.
Install web application firewall
A web application firewall or WAF acts as a barrier shielding your website from malicious actors infiltrating your website. It identifies and thwarts potential threats in real-time, filtering harmful traffic and allowing only legitimate traffic to pass.
WAFs can protect your site from various attacks including SQL injection, CSRF, XSS, and zero-day and DDoS attacks. Though WAFs are not impenetrable and are not the silver bullet that can stop all security threats, they are nonetheless an essential security toolkit.
Backup your website regularly
Of all the things that could happen, losing website data permanently is the most dreadful. No matter the extreme security measures that are in place, a site is not perfectly safe. A human error or physical damage, for instance, could erase the data.
Backups serve as a safety net and allow you to restore your website to a previous, clean state, minimizing data loss.
Store the backups in a secure location, away and separate from your primary server. Test the backups periodically to check if they can be successfully restored. And if possible, create multiple backups and retain multiple versions to cover a range of scenarios.
Conclusion: Safety first, last, and always
There is a strong case for website security to be taken seriously, not just once, or once in a while. You need to take all necessary action precautions within your means and without. And that may mean occasionally working in concert with a WordPress development company to scrutinize vulnerabilities and fortify your website.
Taking due precaution and preventive measures can go a long way to thwart malicious agents. This is the most fundamental security principle. As the proverb says: Prevention is better than cure.
